|
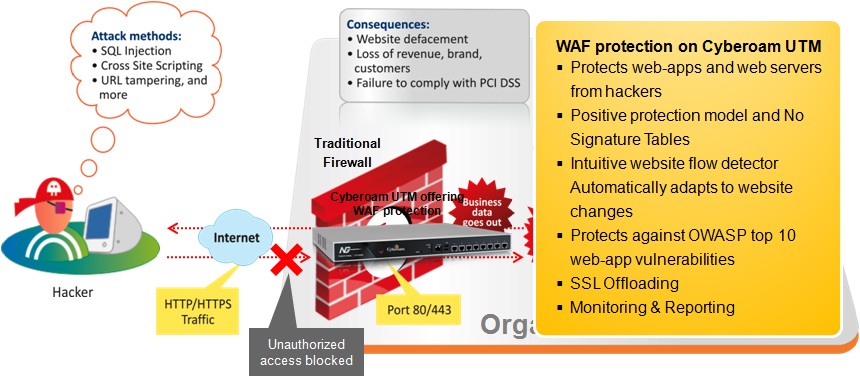
Cyberoam offers Web Application Firewall subscription on its UTM appliances to secure websites and Web-based applications in organizations against attacks such as SQL injection, cross-site scripting (XSS), URL parameter tampering, session hijacking, buffer overflows, and more, including the OWASP Top 10 Web application vulnerabilities.
Cyberoam’s Web Application Firewall module follows the positive protection model based on its Intuitive Website Flow Detector that intelligently “self-learns” the legitimate behavior of Web applications. Based on the Intuitive Website Flow Detector, the Web Application Firewall ensures the sanctity of Web applications in response to server requests, protecting them against Web application manipulation attacks. The Cyberoam Web Application Firewall is deployed to intercept the traffic to and from the web servers to provide an added layer of security against attacks before they can reach the Web applications. It looks at every request and response within the HTTP/HTTPS/Web Service layers.
| Positive Protection model without signature tables |
 |
Works based on the Intuitive Website Flow Detector that “self-learns” Web application behavior to allow intended behavior of Web applications |
| |
| |
|
 |
Protects against known and unknown attacks on Web applications |
| |
| |
 |
Allows proactive security over reactive security |
| |
|
| Comprehensive business logic protection |
 |
Protects against attacks like SQL injection, Cross-site scripting, cookie-poisoning, and more, that seek to exploit business logic behind Web applications |
| |
|
 |
Ensures Web applications are used exactly as intended in organizations |
| |
|
| HTTPS(SSL) encryption offloading |
 |
Secures encrypted (SSL) connections |
 |
Reduces latency of SSL traffic with its SSL offloading capabilities |
| |
|
 |
Protects web applications processing sensitive data in financial services, healthcare, e-commerce and other industries |
| |
| |
| |
 |
Improves performance of SSL traffic |
| |
|
| Instant web-server hardening |
 |
Protects any Web environment (IIS, Apache, WebSphere®, etc.) against more than 14,000 server mis-configurations and third-party software vulnerabilities |
| |
| |
| |
|
 |
Protects against manipulation of Web environment for malicious intentions |
| |
|
| Reverse proxy for incoming HTTP/HTTPS traffic |
 |
Incoming Web application requests from the Web client terminate at the WAF and valid requests are submitted to the back-end Web server, hiding the existence and characteristics of originating servers. |
| |
| |
| |
|
 |
Provides an added level of security by virtualizing the application infrastructure |
| |
| |
|
| URL , Cookie, and Form hardening |
 |
Protects Web application-defined URL query string parameters, cookies, and HTML form field values |
| |
|
 |
Automatically identifies and blocks manipulation of browser data to prevent attempts to escalate user privileges through cookie-poisoning, gain access to other accounts through URL query string parameter tampering, and more |
| |
| |
| |
| |
| |
|
| Monitoring and reporting |
 |
Provides alerts and logs – type of attacks, sources, action taken |
| |
|
 |
Helps comply with PCI DSS regulatory compliance requirements |
|
|